Hackers are constantly looking for ways to exploit software vulnerabilities, and if they can gain access to sensitive data or systems, they can cause a lot of damage.
In this article, we'll introduce you to stride threat modeling, a technique that can help you build secure software by considering how hackers might attack your system.
What is threat modeling?
Threat modeling is a method for identifying and evaluating potential security threats and vulnerabilities in software. Threat modeling can help you identify potential risks and vulnerabilities in your software before they become problems, and it can also help you evaluate how to mitigate those risks.
There are a few things to keep in mind when doing threat modeling:
1. You must be realistic about the risks your software is susceptible to. Don't put all your eggs in one basket by assuming that your software is immune to all security threats.
2. Think about the different ways that malicious actors might try to exploit your software vulnerabilities. Are there specific attacks that you need to worry about?
3. Consider the consequences of a successful attack against your software. What would happen if someone could exploit a vulnerability in your software? Would they be able to access sensitive data or control systems?
4. Think about how users might misuse or abuse your software. What could they do with it that you didn't intend them to do?
What is Stride Threat Modeling?
Stride Threat Modeling is a security method that uses data from past attacks to help developers create more secure software. It helps identify how attackers may attempt to exploit a system's vulnerabilities and help prioritize which vulnerabilities to fix.
How does Stride Threat Modeling work?
Stride Threat Modeling is based on the concept of risk. Each vulnerability can be assigned a risk level, with the highest risk level representing the most likely attack scenario. Attackers will typically try to exploit vulnerabilities with the highest risk levels first.
Once a vulnerability has been identified, Stride Threat Modeling can help determine how likely an attacker will attempt to exploit it.
How do I get started using Stride Threat Modeling?
There is no single way to use Stride Threat Modeling, as it depends on the specific security needs of your software. However, there are some general steps that you can take. First, you need to gather data about past attacks. This data can come from public sources (such as databases of known exploits) or from your reports of possible attacks.
How to use Stride Threat Modeling to build secure software
Stride Threat Modeling is a method for building secure software that takes into account the potential threats to the system. The model can be used to identify a system's risks and vulnerabilities and create a plan for addressing them.
The model can identify the risks and vulnerabilities in a system, including those posed by malicious attackers. It can also be used to create a plan for addressing these risks and vulnerabilities.
The model can identify the risks and vulnerabilities in a system, including those posed by malicious attackers. It can also be used to create a plan for addressing these risks and vulnerabilities.
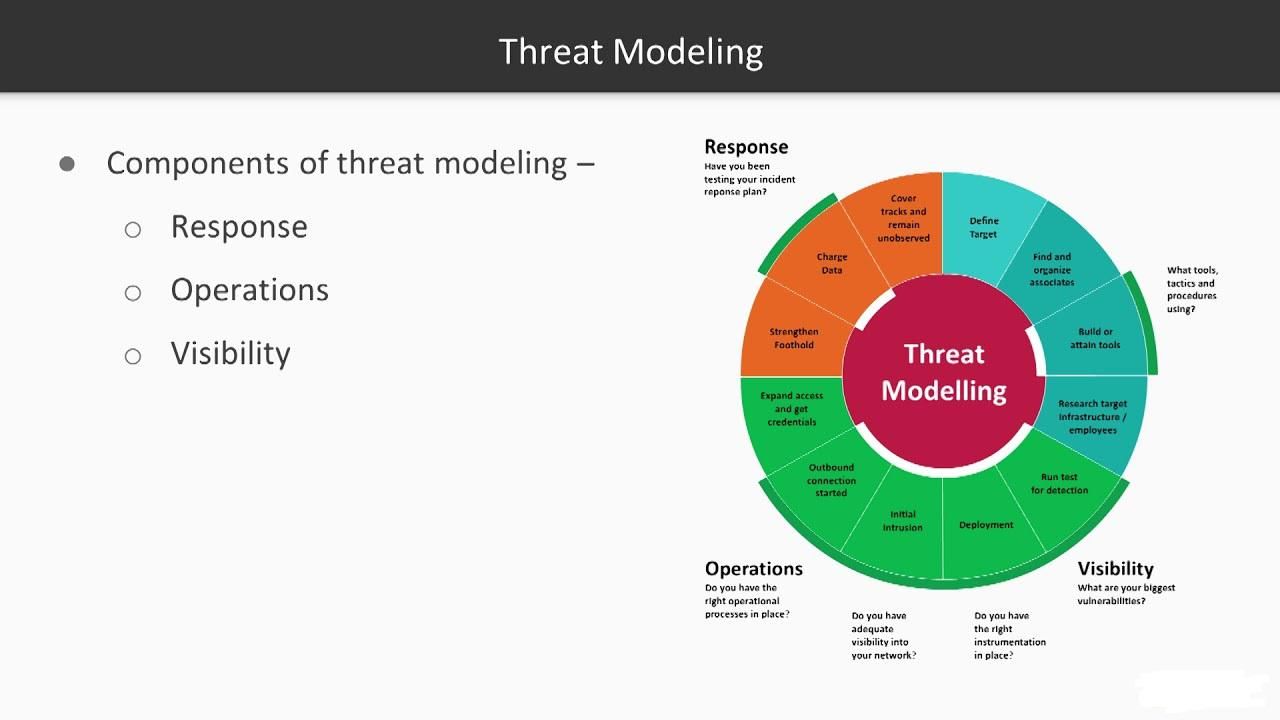
How to Construct a Stride Threat Model for Your Software
Stride threat modeling (STRIDE) is a method for Risk Identification and Risk Assessment that helps organizations assess the potential impact of threats to their software systems. STRIDE focuses on two key aspects of software security: the threats posed by external actors and the threats posed by insiders.
The first step in STRIDE is to identify the different types of threats your software system may be exposed to. This can be done by analyzing your software's architecture and the data it accesses, as well as assessing your software's functionalities. After you have identified the types of threats, you need to assess how likely each one is to occur and what potential consequences they would have if they did.
STRIDE can be used to help build a secure software system by identifying which vulnerabilities are most likely to be exploited and developing countermeasures to protect against them. By doing this, you can create a more resilient system that is less likely to be compromised by malicious actors.
What are the Benefits of Using a Stride Threat Modeling?
There are many benefits to using stride threat modeling in software development. Stride helps to identify potential risks and vulnerabilities in the software and can help to create a secure development process. Additionally, it can provide a better understanding of the overall system, which can help to ensure that the software is reliable and secure.
Conclusion
Software security is an increasingly important topic for large companies, small businesses, and individual users. In this article, we will discuss the basics of stride threat modeling, a technique that can help you build secure software. By understanding how attackers think, you can create more effective defenses and are less likely to be bypassed. I hope this article has helped you understand stride threat modeling better and given you some ideas on how to put it into practice in your software development projects.




 Going to the cinema alone is good for your mental health, says science
Going to the cinema alone is good for your mental health, says science












 women in street dancing
Photo by
women in street dancing
Photo by  man and woman standing in front of louver door
Photo by
man and woman standing in front of louver door
Photo by  man in black t-shirt holding coca cola bottle
Photo by
man in black t-shirt holding coca cola bottle
Photo by  red and white coca cola signage
Photo by
red and white coca cola signage
Photo by  man holding luggage photo
Photo by
man holding luggage photo
Photo by  topless boy in blue denim jeans riding red bicycle during daytime
Photo by
topless boy in blue denim jeans riding red bicycle during daytime
Photo by  trust spelled with wooden letter blocks on a table
Photo by
trust spelled with wooden letter blocks on a table
Photo by  Everyone is Welcome signage
Photo by
Everyone is Welcome signage
Photo by  man with cap and background with red and pink wall l
Photo by
man with cap and background with red and pink wall l
Photo by  difficult roads lead to beautiful destinations desk decor
Photo by
difficult roads lead to beautiful destinations desk decor
Photo by  photography of woman pointing her finger near an man
Photo by
photography of woman pointing her finger near an man
Photo by  closeup photography of woman smiling
Photo by
closeup photography of woman smiling
Photo by  a man doing a trick on a skateboard
Photo by
a man doing a trick on a skateboard
Photo by  two men
two men  running man on bridge
Photo by
running man on bridge
Photo by  orange white and black bag
Photo by
orange white and black bag
Photo by  girl sitting on gray rocks
Photo by
girl sitting on gray rocks
Photo by  assorted-color painted wall with painting materials
Photo by
assorted-color painted wall with painting materials
Photo by  three women sitting on brown wooden bench
Photo by
three women sitting on brown wooden bench
Photo by 
 Photo by
Photo by  Photo by
Photo by  Photo by
Photo by  Photo by
Photo by 


 people sitting on chair in front of computer
people sitting on chair in front of computer