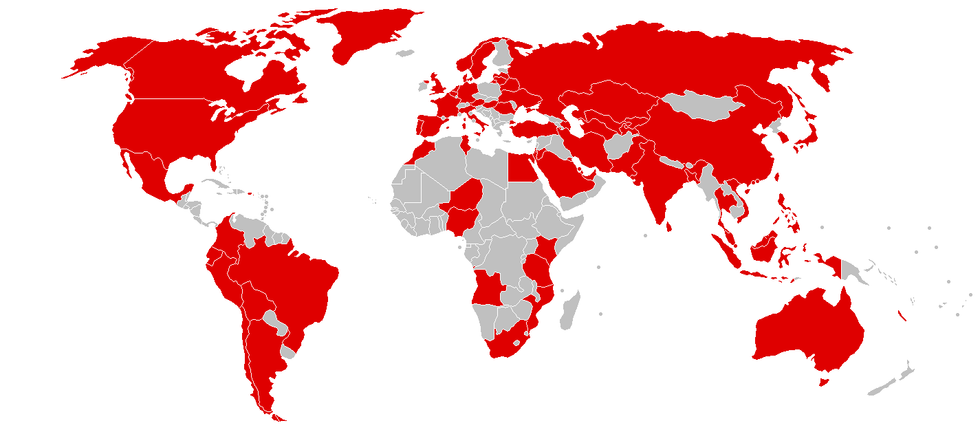
On May 12, 2017, a cyber attack struck worldwide with many people falling victim to a malware under the name "WannaCry." The cyber attack affected more than 230,000 computers in 150 countries, demanding ransom payments in the Bitcoin currency. Businesses affected by this attack include Britain’s National Health Service, FedEx, Deutsche Bahn, and LATAM Airlines.
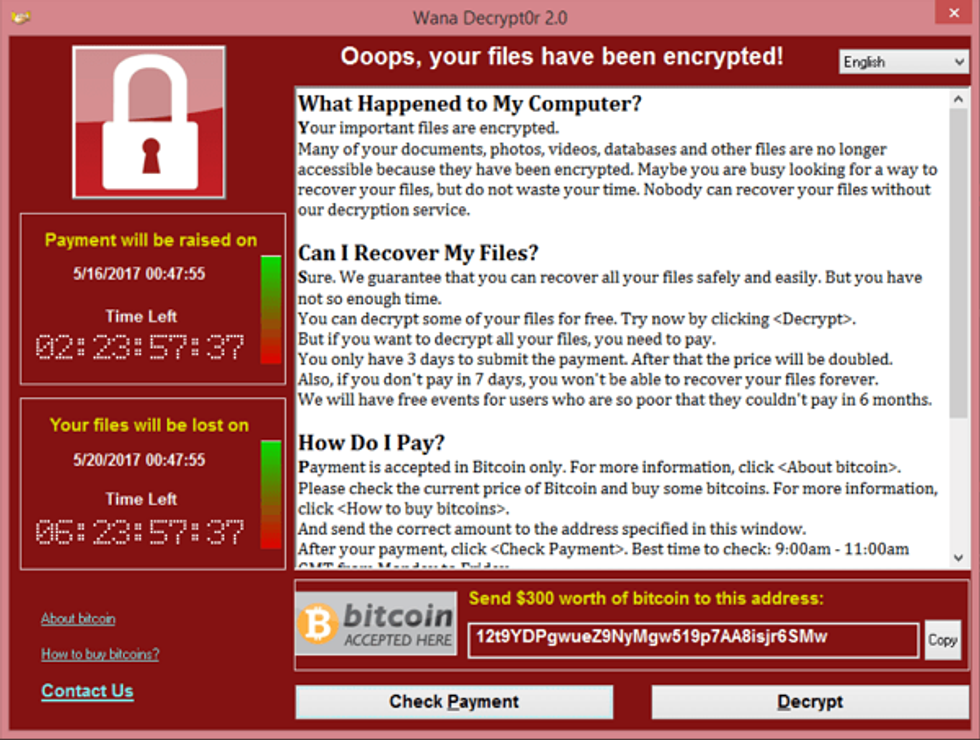
WannaCry, also going under the name of WannaCrypt, WannaCrypt0r 2.0 and Wanna Decryptor, is a type of ransomware program that targets Microsoft Windows operating systems.
A ransomware is a type of malware that blocks access to data until a ransom is paid and displays a message requesting payment to unlock it. Most basic ransomware may lock the system making it difficult for someone unfamiliar to ransomware to reverse. Advanced ransomware, such as WannaCry, encrypts the victim’s files making everything inaccessible and demands a ransom payment to decrypt them. Typically, ransomware attacks are carried out by a Trojan Horse virus, another form of malicious malware.
Similar to other ransomware, the initial infection of WannaCry was either through a vulnerability in the network defenses or a well-crafted phishing attack, the attempt to obtain sensitive information such as usernames, passwords, or even credit card information. Specifically, the ransomware uses the EternalBlue exploit and DoublePulsar backdoor which were both developed by the U.S. National Security Agency (NSA) and leaked by The Shadow Brokers hacker group in early 2017. The ransomware then spreads through a network which has not installed recent security updates to directly infect any exposed systems.
When WannaCry is executed on an infected computer, a message is displayed informing the user that their files had been encrypted and demands a payment of around $300 in bitcoin within three days. If the transaction is not completed with the given time, the ransom doubles to $600.
The cause of the WannaCry virus was within the Windows operating system by which Microsoft had released a security patch on March 14, 2017, nearly two months before the attack. The security patch modified the Server Message Block (SMB) protocol used by Windows. Organizations that lacked this security patch were affected by WannaCry and furthermore, any organizations still running on an older operating system, Windows XP, were at a higher risk in particular, due to the operating system being unsupported with no security updates released since April 2014. However, after the attack, Microsoft has released a security patch for Windows XP on May 13, 2017, the day after the attack launched.
The European Union Agency for Law Enforcement Cooperation had deemed the attack “unprecedented,” with many affected by the attack such as the many hospitals in England and Scotland, and devices including computers, MRI, blood storage refrigerators and theater equipment were affected.
Several hours after the initial release of WannaCry, a researcher and blogger under the name of MalwareTech accidentally discovered a “kill switch” deep within the source code of the malware. By registering a domain name to create a DNS sinkhole, the attacks stopped spreading and although this did not help already infected systems, it slowed the spread of any further infections and gave time for defensive measures to be deployed worldwide.
On March 14, 2017, a patch that had been deemed “critical” was issued by Microsoft in order to remove hidden vulnerabilities to supported systems. In addition, users who run the older, unsupported operating systems such as Windows XP and Windows Server 2003 were issued patches as well.
On May 16, 2017, researchers from University College London (UCL) and Boston University (BU) reported that their "paybreak" system could defeat WannaCry and several other families of ransomware. On May 19, 2017, a group of French security researchers reported that they had found a way to unlock the program without paying the ransom demand. Several other tools have been released to help protect against the WannaCry malware, including WannaSmile, which disables the SMBv1 protocol which implementations embed the flaw and WannaPatch that detects if a system is vulnerable and, if so, automates the downloading of the needed patch.
Within four days of the initial outbreak, security experts were saying that most organization had applied updates and that new infections had slowed down.
For those whose machines have not been infected, it is advised to do these steps right away:
- Apply the Microsoft patch that will thwart the attack. It’s available here.
- Check for any available Windows update.
- Update your antivirus to the latest version and perform a system scan.
- If you can, backup your data through a cloud or an external drive.
As of May 24, 2017, the WannaCry ransomware has stolen 49.775 BTC which equates to roughly $123,040.
For those interested, there is a live map of all botnets that are currently affecting the world in real-time here.