Several times over the past year you may have heard about NSA computer surveillance tools and code being publicly leaked. An anonymous hacker group known as The Shadow Brokers recently took credit and even tried to auction off these tools.
Imagine stealing a few missiles from an army base and putting them up on eBay. This is no less serious.
"This is quite possibly the most damaging thing I've seen in the last several years.
This puts a powerful nation-state-level attack tool in the hands of anyone."
Matthew Hickey, Hacker House
This past weekend, version 2.0 of the WannaCry ransomware utilized the hacking power in those NSA leaks to infect hundreds of thousands of computers around the world. Not just your grandma's computer either. This attack locked computers at factories, hospitals, and institutions for a few days until being heroically crippled thanks to the hard work of one independent security researcher.
So what the hell is going on? What's ransomware and why does it make me WannaCry?
That's our Tech Translation topic, class is in session.
So what happened?
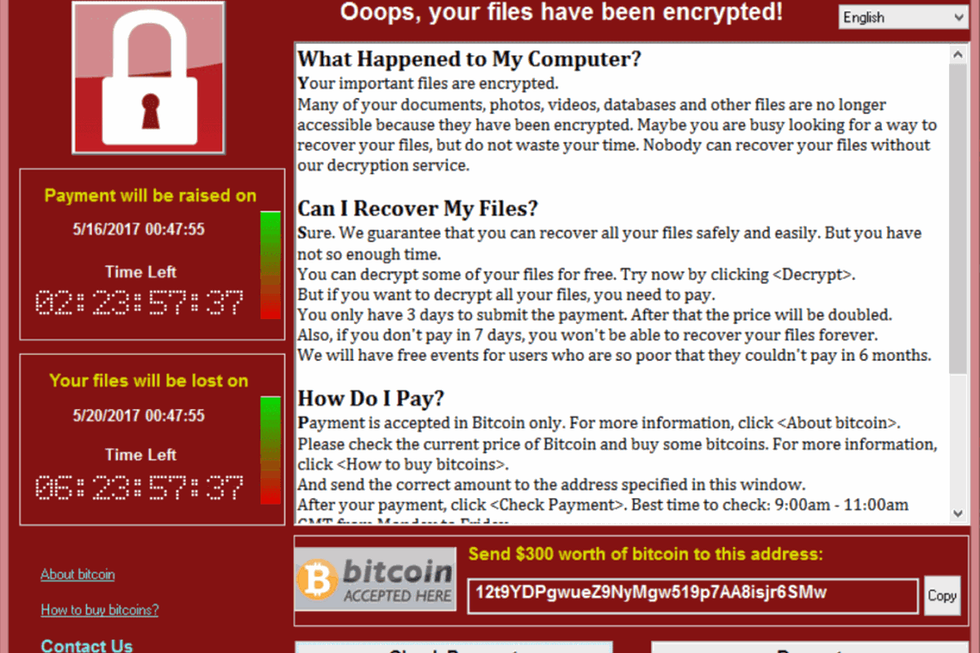
Ransomware is a particularly nasty type of computer malware. Once inside a system, the program takes your data hostage (or at least pretends to) until a ransom payment is made to the attackers, usually via hard-to-trace online currencies like Bitcoin.
The WannaCry authors took this to the extreme by encrypting your data until a payment is made.
PRO TIP: if ransomware happens to you, don't ever pay. What incentive do criminals really have to keep their word and restore your files? Zero.
When used by the good guys, encryption is a standard security practice. It basically scrambles your data into an alien language behind the scenes so anyone without a proper key can't read it. Ransomware will send that key back to its master before deleting itself, leaving you to sit there with your mouth open.
After the initial batch of infections, most likely through spearphishing attacks, WannaCry used the Windows SMB vulnerability information and tools stolen from the NSA to bypass normal security measures and spread automatically to other computers. That's what made this so horrible.
The NSA used these vulnerabilities for years without telling Microsoft. Computers running older versions of Windows like XP, 7, 8 and Server 2003 were at the highest risk. Microsoft actually released a security patch in March this year to address these vulnerabilities when they leaked, even for XP the day after the attack.
The problem is that so many machines around the world had not been updated to that critical security patch and remained vulnerable.
Needless to say, Microsoft is furious with the NSA.
Who done it?
Nobody's really sure right now. We can assume it's the same authors as WannaCry 1.0, which did not utilize the NSA tools and failed to spread effectively.
Russian malware typically tries to avoid infecting fellow citizens, but WannaCry doesn't mind infecting computers set to Cryllic (Eastern Europe / North and Central Asia). Time-stamps in the code suggest maybe Japan, Indonesia, Korea or far East China / Russia.
Other evidence points to a new group of amateur hackers. For instance, hundreds of thousands of victims were hit around the world. Even Trevor Noah had a WannaCry segment on his March 15th evening show. Not so subtle; law enforcement is pissed.
Also, only a $300 ransom? Psh. I would have demanded at least $500. Noobs.
If it's so scary, why aren't we all infected yet?
Like I said, updated computers didn't have much to worry about. Windows 10 has the fixes already. This was more of a problem for larger organizations or lazy people.
Also, one security researcher Marcus Hutchins, known as MalwareTech, found the hidden Achilles Heel.
To analyze and observe malware in action, programs are confined to little digital jail cells known as virtual machines: Windows inside of Windows. They can run but cause no harm. It's standard practice.
Remember Volkswagen's diesel emission scandal? Cars could detect when they were being inspected and started operating differently to pass. Malware can have similar features.
To know if their virus is being inspected, one method is to make it call out to one or more random URLs. When inside a jail cell, the reply would be the same "YES" for all addresses and the virus will basically shut down to avoid study. If not being inspected, those calls should return as "NO" and it would try and spread further.
In this case, when Marcus saw the URL being called he immediately registered it for like $10. This caused every instance of WannaCry around the world to think it was being inspected and stop spreading.
This gave other countries, organizations and security buffs some more time to get a handle on the situation. The authors could have registered it themselves, but didn't. Noobs.
Check out his whole blog write-up here.
Aftermath
The bitcoin addresses given by the thieves are being monitored. Bitcoin might be "anonymous" and decentralized, but transaction information is still publicly recorded. With enough study, patterns and identities could be discerned in time.
The National Health Services (NHS) of England and Scotland were hit hard with up to 70,000 devices including computers, MRI scanners, and blood refrigerators being affected. Some NHS services had to turn away non-critical emergencies and ambulances for a time.
Some factories and companies shut down for a day to stop it from spreading further and perform cleanup. Bloomberg has an article detailing more about affected entities.
Microsoft denounced the NSA for hoarding information like that. Ultimately it causes more harm than good when things reach the wrong hands. They want the world to see this as a warning. If a few amateurs can accomplish this, imagine what a team of veteran hackers could accomplish.
That's all folks. Hopefully, you learned to keep your machines updated.
Drop a comment or reach out on social media to discuss with me.
@pjmulroe #MakeSecurityGreatAgain #WannaCry
https://www.troyhunt.com/everything-you-need-to-kn...